Written By:
rwilliams
Identity, trust and security are at the heart of enterprise digital transformation, making it easier and faster to engage customers and partners, create amazing experiences and offerings and level up operations. Security is now a true business enabler. Here are 8 steps to implement a holistic approach to managing physical and logical identities for employees, contractors, vendors and visitors to align security with business goals and reduce enterprise risk.
As digital systems are controlling more and more of our critical infrastructure, security convergence now encompasses IT, Physical Security, Operational Technology (OT) and IoT, all rolled-up into Cyber-Physical. Physical Identity Access Management (PIAM) can address all identities across the entire enterprise and is the cornerstone of a secure and compliant experience for workforce, visitors and contractors. A converged solution that integrates with HR systems, IT, OT and Physical Access Control Systems (PACS), delivers the ability to assign specific roles-based logical and physical access – a foundation for a cyber-physical approach. With a converged security technology platform your Security Operations Center (SOC) can deliver a unified and proactive threat response to a wide range of incidents – with real-time data connection across enterprise applications
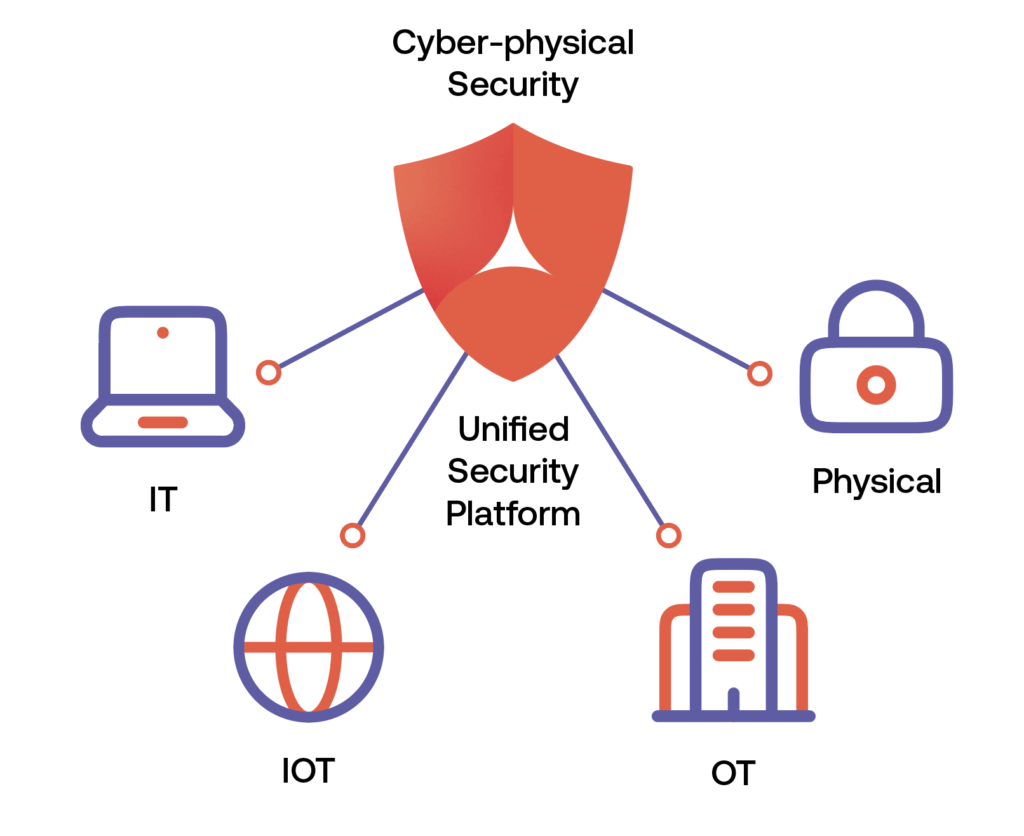
Unified security must extend beyond IT and include OT and physical security controls. New converged cyber-physical security models detect security gaps that go undetected by conventional IT-only security automation tools. You can manage the complete identity lifecycle from onboarding to offboarding for your internal and external workforce, visitors and contractors and tie it directly to access governance for IT, physical and OT workspaces. Automated workflows allow security and IT department managers to quickly approve or deny access requests while actively enforcing company policies and satisfying compliance and industry regulations.
Key capabilities include:
Alert Enterprise software enables organizations to fully integrate their IT systems with OT, not only for provisioning but also for monitoring and correlation of blended threats in a truly converged approach. IT and OT managers can define, tailor and enforce policies – closing gaps and minimizing risk of uncontrolled access to sensitive or mission critical areas.
Key capabilities include:
Read the IT-OT Convergence e-book
Your compliance department wants to make the auditors happy and reduce the amount of time and effort it takes to report. With PIAM, built-in controls automate the compliance process, adhering to all industry regulations and corporate policies. Automatic verification of training and background certification deliver real-time rule enforcement. And when requirements are not met, access can be automatically revoked. Compliance and Active Policy Enforcement features enable you to easily and consistently meet regulatory requirements. In addition, you can now enable roles-based and individual user-based access to critical assets based on identity profile attributes.
Key capabilities include:
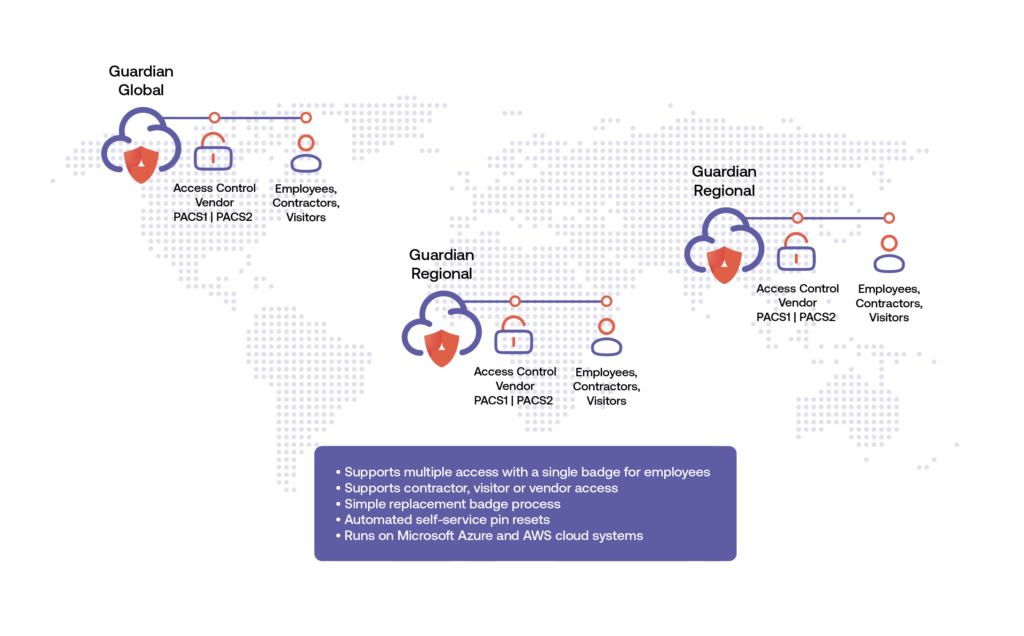
The latest software solutions are designed to scale to hundreds of thousands of users for large enterprise and mission critical applications. In one example, a government agency uses PIAM software from Alert Enterprise to globalize their deployment, cover 18 different time zones and unify security policies across 200 countries. Powerful and flexible technology platforms aggregate reporting and stats from all locations, with high availability enterprise fail-over and backup. Secure on-premise or cloud-based SaaS architecture supports global deployment and scale.
Key capabilities include:
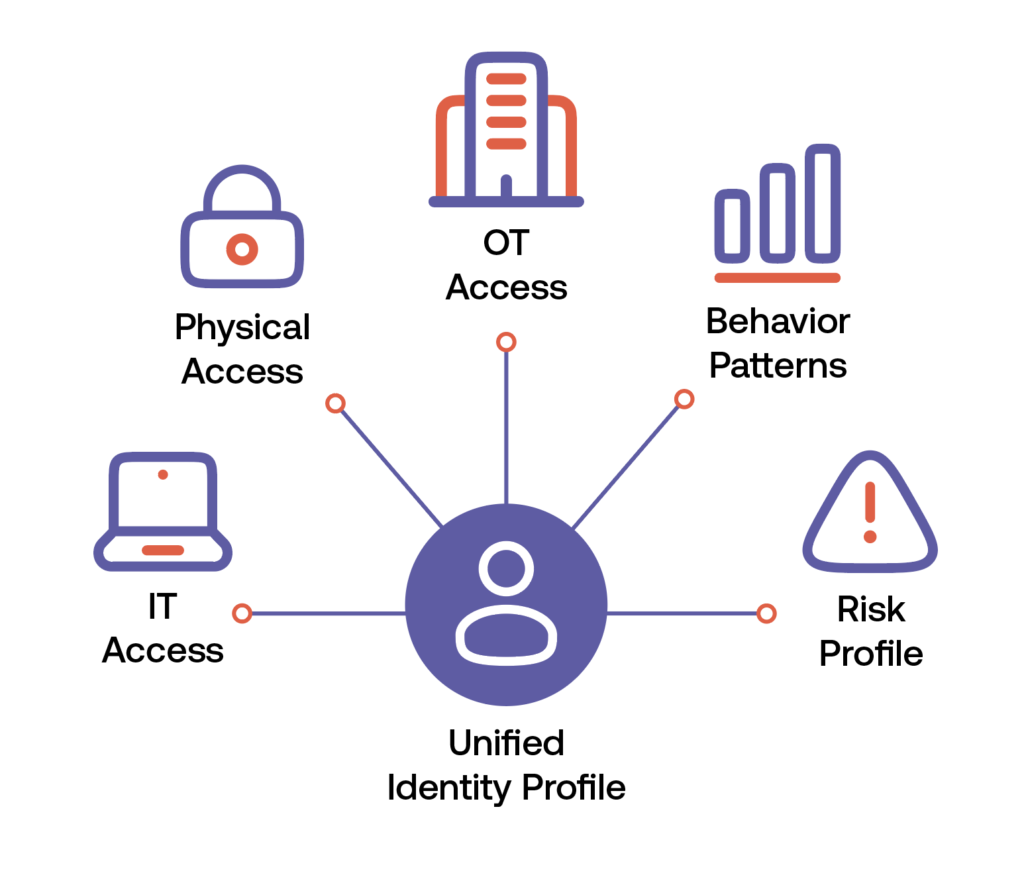
Purpose-built risk analytics and risk management features go beyond traditional badging solution capabilities. Identity Intelligence technology arms your threat hunters with data on user attributes, access patterns and even policy violations you can use to establish identity risk scores. Embedded access behavior monitoring automatically detects anomalies and sends alerts on exceptions. With customizable reports and dashboards, enterprises stand ready to mitigate and prevent blended cyber-physical insider threats.
Key capabilities include:
One might say it was only a matter of time: We have been digitizing our physical world, blurring the lines between physical and cyber spaces. Cyber-incidents can now have direct impact on physical assets and processes and vice versa. PIAM software enforces best-practice cyber protection for systems across physical security, OT, IT and automation. Even cyberattacks on legacy and migrated physical access control system (PACS) components are part of real-time monitoring: alerts are created from unauthorized configuration changes or when badges or identities created in the PACS backend database bypass or circumvent standard operating procedure or company policies. Explore Enterprise Sentry unified threat response platform.
With the digital transformation, new intelligence comes to light in the workspaces we secure. Recent studies show that managing 60% of enterprise workspace more effectively can add 20% to your bottom line every year. PIAM from Alert Enterprise delivers added data with Workspace Intelligence, facility-wide utilization insights for the enterprise to optimize available space. Workspace Intelligence enables organizations to automatically capture and measure building occupancy, utilization and optimization data to identify areas of cost reductions, efficiency improvements and potential revenue streams. More effective space utilization translates into real dollar savings for the enterprise and a stronger bottom line.
Discover how security can become your business enabler.
Key capabilities include:
Take your next step and request a demo today.

Director de estrategia
David Cassady lleva más de 30 años vendiendo y dirigiendo equipos en Silicon Valley. Durante ese tiempo, ha dirigido una mezcla de empresas de software ya establecidas y startups. Cassady también ha participado en cinco OPIs, y al menos en otras tantas adquisiciones.
Como director de estrategia, David aprovecha su amplia experiencia ayudando a las empresas de software a impulsar el crecimiento a través de profundas e impactantes asociaciones con los proveedores de SaaS más exitosos del mundo, como ServiceNow, Microsoft y SAP.

Director de seguridad
Vicepresidente sénior, Regulated Industries
Mark Weatherford aporta a Alert Enterprise años de experiencia en el ámbito de la ciberfísica de alto nivel y, como director de seguridad (CSO), dirige la estrategia de gestión y protección de datos, asesorando las políticas y procedimientos de seguridad ciberfísica dentro de la empresa. Weatherford también trabaja en colaboración con empresas y profesionales ejecutivos de los sectores de la ciberseguridad y la seguridad física para acelerar aún más la adopción de la convergencia de la seguridad.
Mark ha ocupado numerosos cargos de alto nivel centrados en la ciberseguridad, entre los que se incluyen el de vicepresidente y director de seguridad de la Corporación Norteamericana de Fiabilidad Eléctrica (NERC), el de primer subsecretario adjunto de ciberseguridad del Departamento de Seguridad Nacional bajo la administración Obama, el de primer director de seguridad de California y el de primer CISO del estado de Colorado.

CTO
Como director de tecnología (CTO) de Alert Enterprise, Harsh Chauhan es responsable de la innovación tecnológica en ingeniería y de la entrega de soluciones de la empresa. Veterano y líder tecnológico con 20 años de experiencia, Chauhan se centra en el crecimiento de la plataforma en la nube a hiperescala 3D Governance Risk Compliance (GRC) de la empresa.
También sigue desarrollando soluciones integradas con socios tecnológicos líderes como SAP, SAP NS2 y ServiceNow. Antes de Alert Enterprise, el Sr. Chauhan ocupó varios puestos de CTO, así como de Product Owner y jefe de desarrollo en SAP GRC 10.0, ofreciendo soluciones específicas a clientes SAP de alto perfil.

COO

CFO y cofundadora
Como directora financiera (CFO) y cofundadora de Alert Enterprise, Kaval Kaur dirige todas las operaciones financieras y administrativas de back-office. Kaur es miembro de la organización profesional nacional American Institute of Certified Public Accountants (AICPA) y de la California State CPA Society.
Antes de incorporarse a Alert Enterprise, fue directora financiera y cofundadora de Virsa Systems, cargo que ocupó hasta su adquisición por SAP.
Kaur es una filántropa apasionada, que abraza la diversidad de la zona de la bahía de San Francisco ayudando y promoviendo actos culturales especiales. Recientemente, ha patrocinado 2000 escuelas públicas en la India rural para impulsar la alfabetización informática de los niños y es madre adoptiva de un niño de 10 años.

Fundador y CEO
Al frente de la transformación digital y la convergencia de la seguridad está Jasvir Gill, fundador y CEO de Alert Enterprise, Inc. Como consumado ingeniero de profesión, Gill está impulsando la transformación digital del sector de la seguridad física, pendiente desde hace tiempo.
Antes de lanzar Alert Enterprise, Gill fue fundador y CEO de Virsa Systems, donde hizo crecer la empresa hasta convertirla en líder mundial de software de seguridad de aplicaciones. Uno de los pioneros en establecer la gobernanza, el riesgo y el cumplimiento como un segmento del mercado del software, impulsó un crecimiento exponencial en Virsa, facilitando su adquisición por SAP en 2006.
En su tiempo libre, Jasvir ayuda a impulsar el empoderamiento social y económico de la comunidad. También es patrono de la Fundación Americana de la India.