Access rules the security landscape.
Every attacker wants it, and every employee has it. It’s time to wipe out silos across HR, IT, OT and physical security and keep identity at the core of your physical access management strategy. You’ll create a smoother employee experience and boost everyone’s productivity on the job.
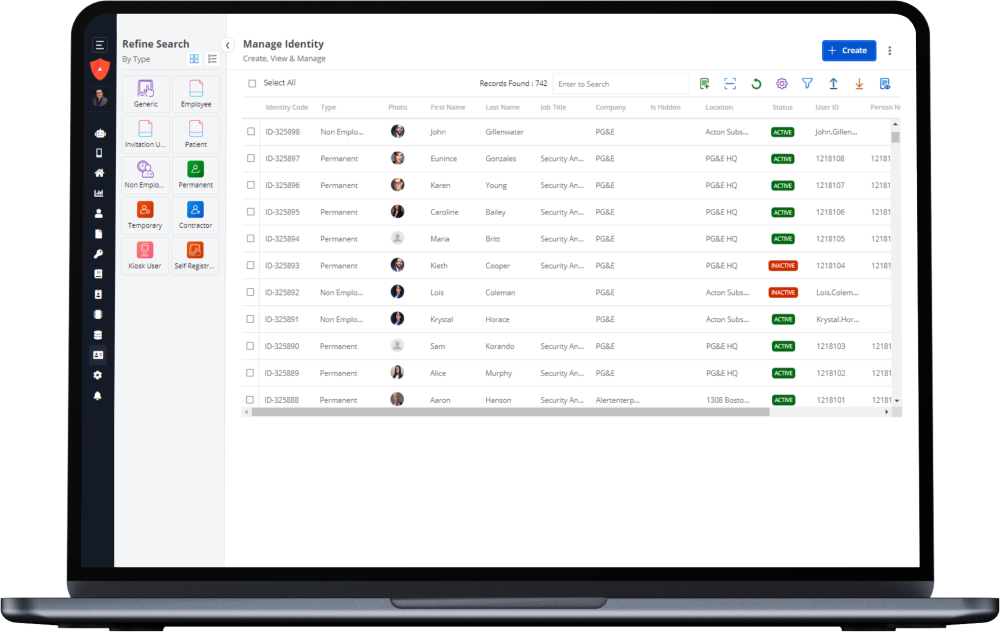
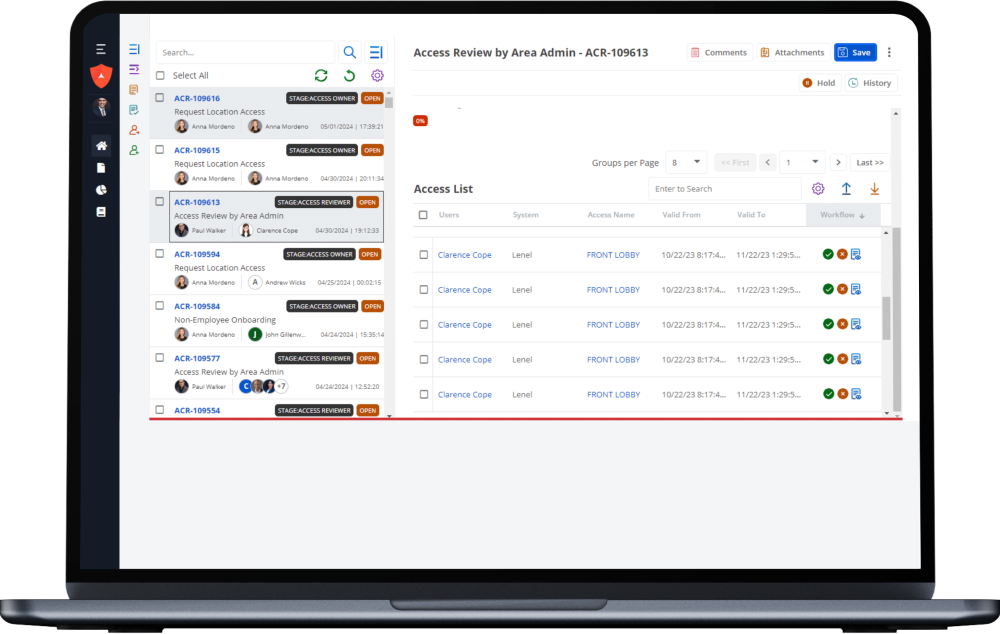
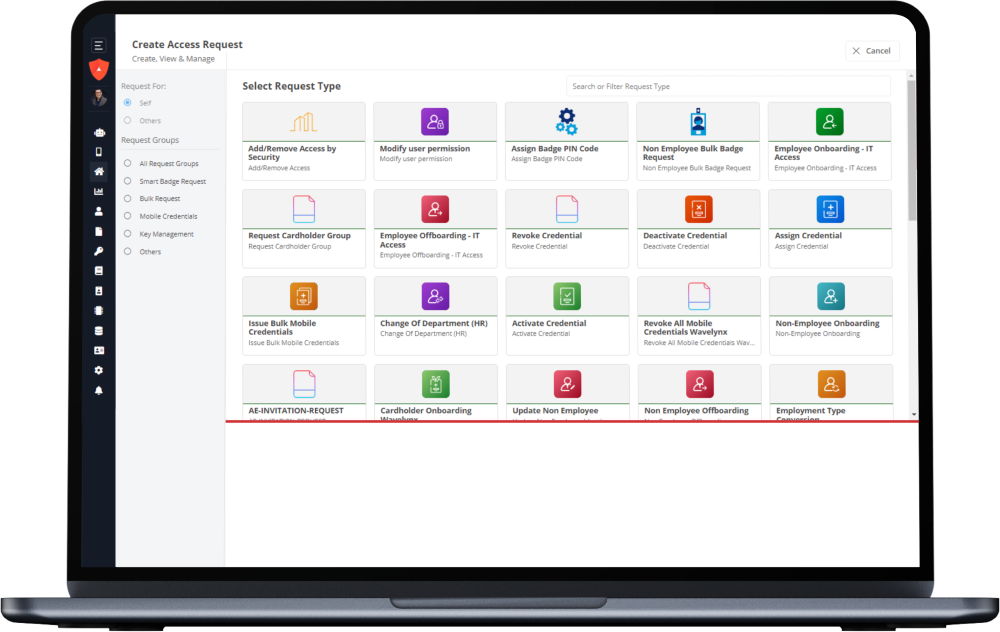
Access every benefit.
- Remove discrepancies between physical and digital employee identities
- Introduce or streamline badging in & out of physical workspaces
- Maintain control over who goes where – and when – with security automation
- Create a frictionless, secure workspace access experience from hire to retire
- Empower employees with self-service options
- Reduce the number of help requests for physical security
- Automate manual, labor-intensive & error-prone tasks
- Use your existing systems to deploy our solutions
- Redirect employees to higher-value work
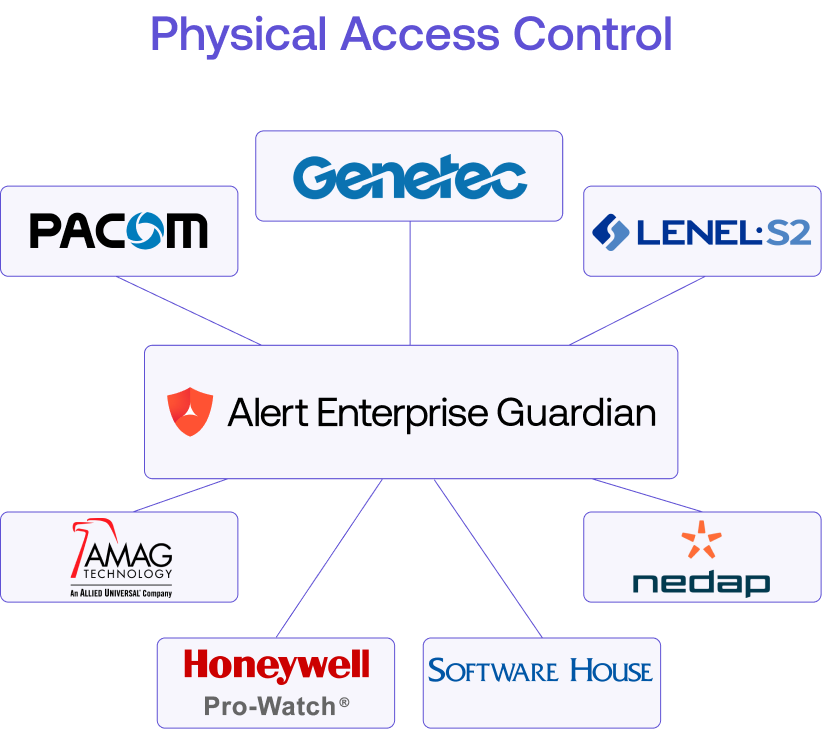
Skip the custom integration.
Need to get going, fast? With out-of-the-box connectors to leading PACS, HR and IT systems like Active Directory, you don’t have to worry about added coding or overhauling your infrastructure.
Unify and streamline your access experience.
Our convergence platform is fully adaptable to fit your organization’s needs. And with these intuitive, built-in capabilities, you’ll be on your way to smarter, safer spaces in no time.
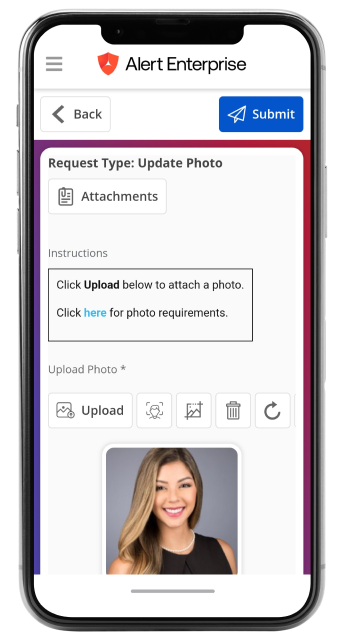
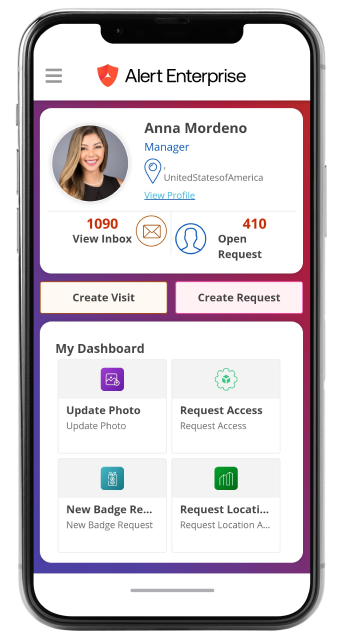
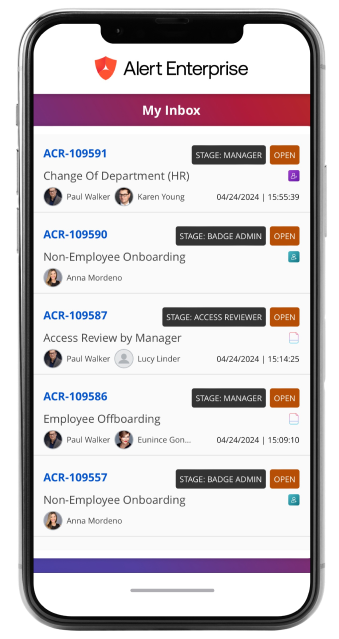
<span data-metadata=""><span data-buffer="">User-Centered Approach
With our drag-and-drop configuration and one-click operation, we prioritize customizability and convenience in our low/no-code platform.
<span data-metadata=""><span data-buffer="">Optimal User Experience
Our platform is designed with the user in mind, blending into your environment for intuitive, seamless interactions.
<span data-metadata=""><span data-buffer="">Self-Service Access Management
Empower your team with easy-to-use tools and automated services that transform day-to-day workflows.
<span data-metadata=""><span data-buffer="">Mobile Devices UI Design
Take a mobile-first approach, allowing both your employees and visitors to easily (and securely) access authorized areas, check in and submit necessary forms – all from their personal devices.


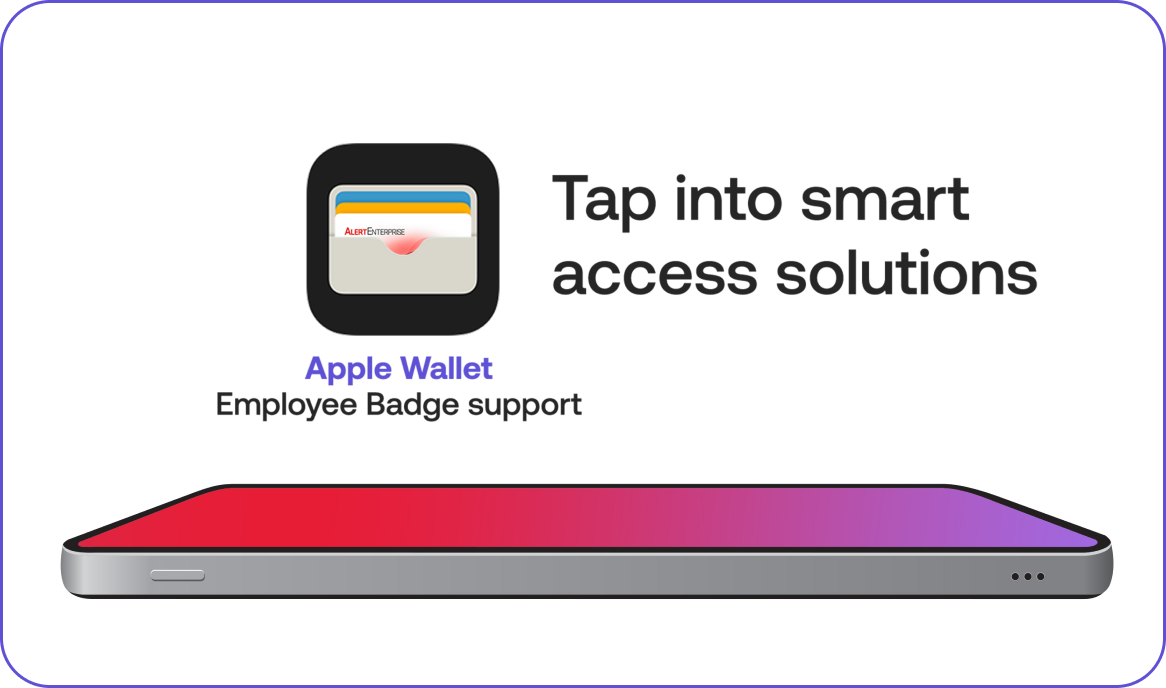
NFC Wallet Mobile Credentials
Replace those plastic physical access cards with a smarter and convenient alternative right inside Apple, Samsung and Google Wallet.
The gift that keeps on giving. Uncover more benefits for your…
- Before Alert Enterprise
- After Alert Enterprise
- Manager manually sends email request for new employee badge and access setup, without knowledge of training status or other prerequisites.
- Automatically informs managers of new hires and assigns role-based access, aligns prerequisites and creates work items for badging office.
- If additional access is needed for specific use cases, access must be requested as an exception. Oh, and without visibility into their team’s access profile.
- Self-service portal enables standardized process to request, approve and ensure policy enforcement (SOD’s, transfers, trainings, safety) and access assignments—with visibility into team’s access data.
- Post submission: No insight into process completion leads to errors and duplication of work.
- Insight into audit trail and workflow; integrates with HR, PAC, training and safety-check systems.
- Complex and manually driven process for contractor onboarding, ongoing management and off-boarding.
- Portal to onboard contractors and vendors with badge, access and policy enforcement—plus notifications for badge/access/training expirations.
- First, facility owner manually requests information from security team as to who has access, then contacts manager to find out why.
- Self-service facility/area owner pods: Visibility into who has access and where, with insight into identity profile and history of actions.
- Offline email/ticket-based approvals are maintained in separate, siloed systems.
- Automated workflow-based approvals with integrated prerequisites in one place.
- Separate follow-up threads to training teams and compliance teams to ensure adherence to safety and compliance.
- Eliminates redundancy and streamlines communication with centralized management of identity, audit trail and compliance/policy checks.
- Heavy reliance on security teams for reporting, dash-boarding, governance and access attestations—with limited visibility into identity profile.
- No reliance on security teams; systems are integrated/automated, with timely notifications, task creation/monitoring and escalations.
- Rely on security team to correlate movement tracks to incidents and provide population data.
- Self-Service: Detailed, near real-time reporting on badge usage for incident correlation and tracking.
- Manual process to maintain compliance and policy enforcement.
- Built-in checks in the system to PROACTIVELY enforce compliance and policy requirements.
- Manpower-intensive with delays to identify any segregation of duties (SOD) and high-risk access, which are typically found post assignments.
- Built-in defined rules and workflow processes to automate any segregation of duties (SOD), high-risk or toxic combination against new/existing access.
- Reliance on other teams to consume/align/correlate compliance conformance and report on safety incidents.
- Centralized view of all access-related processes, with compliance and policy checks, audit trails, approvals and conformance.
What’s happening in unified access management?
Let’s open doors.
Getting in the building has never been so important—or complicated. Let’s simplify with cyber–physical solutions that use the systems you already have.





